UIS.401.2 Data Destruction Guidelines
In support of UIS 401 Data Protection and Security Policy
In order to ensure Georgetown University data is protected throughout its lifecycle and to minimize unauthorized exposure to the that data, the following data removal and destruction requirements must be adhered to in all instances, including, but not limited to:
- A technology asset is removed from service for:
- end-of-life or end-of-support donation or destruction
- third-party repair or support
- The data retention rules dictate that data must be removed
- Applicable data use agreements or protocols require that study or research-related data must be deleted
- 3rd-party access to moderate-risk and high-risk data includes provisions to dispose of data upon service termination
Data Destruction
Upon Decommission of Assets
GU devices cannot be donated, transferred, or disposed of without evidence of UIS data sanitization activities prior to disposal.
- Purge or securely wipe data using following applicable methods to ensure the data is unusable, inaccessible, and unable to be reconstructed
- Erasing by overwriting: Erasing by overwriting is a way of scrubbing data with random overwrite patterns – not just all zeros or another single character. A minimum of three (3) overwrites is required for the data to be erased.
- Degaussing: Degaussing is the process of erasing all the data previously written to the hard drive or tape by demagnetizing where the magnetic charge of an object is re-set to a magnetically neutral state.
- Destruction: If data cannot be overwritten or degaussing is not possible, hard drives must be physically destroyed. For drives that are defective, dead, or sufficiently unresponsive that they do not complete at least three overwrite minimum, physical destruction is required.
- Transfer all useful University data from each hardware asset to an approved University file sharing system or departmental folder before the asset is repurposed or removed from University service.
- Install generic image if hardware asset is permitted for donation or transferred externally, including trade-in or replace as part of a warranty or repair contract.
- Remove all licensed, or Georgetown-specific software or operating systems from hardware asset. Attestation of erasure of licensed software and the University data is required for periodic audit purposes.
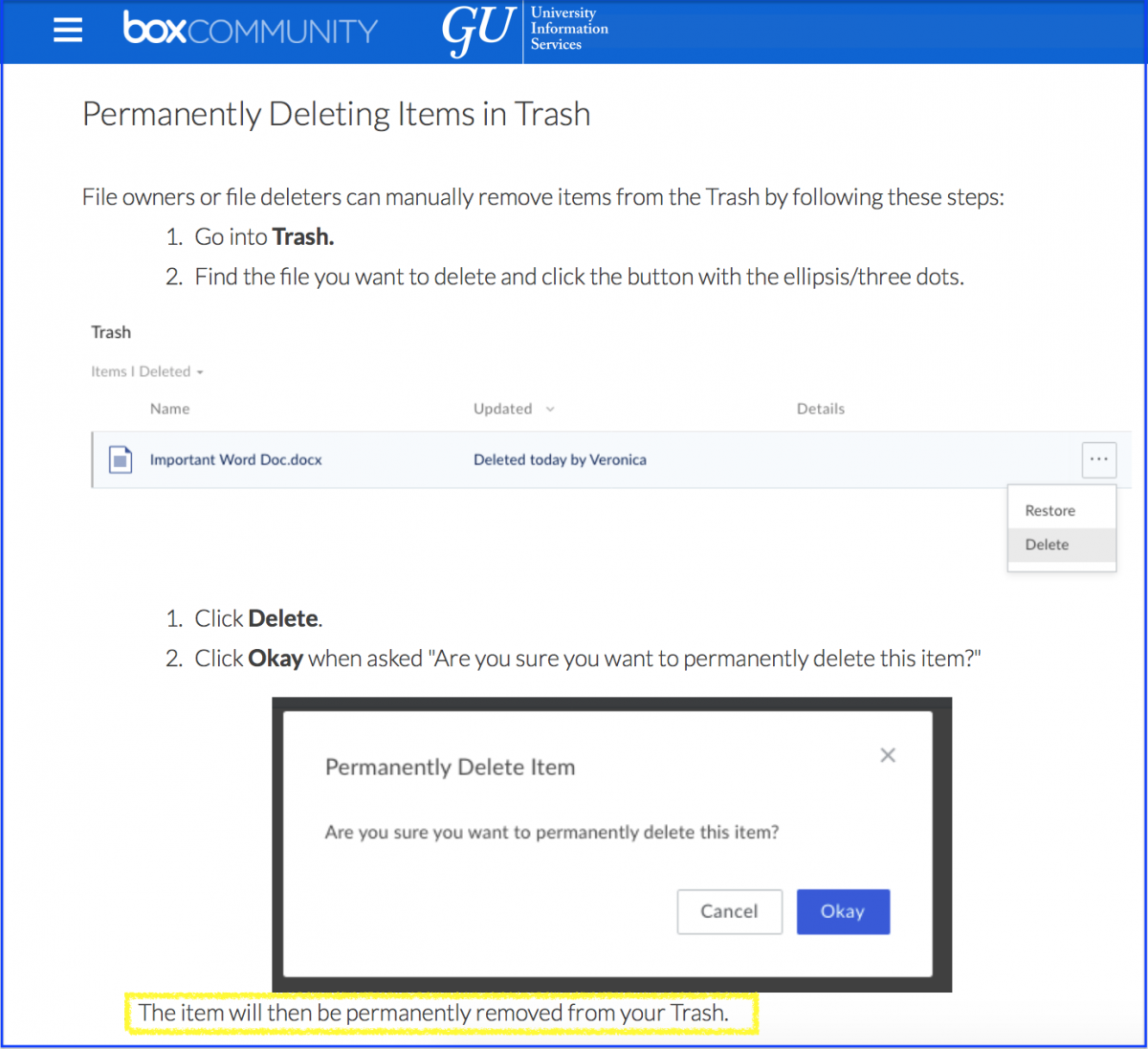
Upon Removal from GU Box
- Delete the files and folders that are required to be removed
- Access the “trash” and delete the files and folders from the trash repository (user must be a folder “owner” or “editor” in order to delete data)